






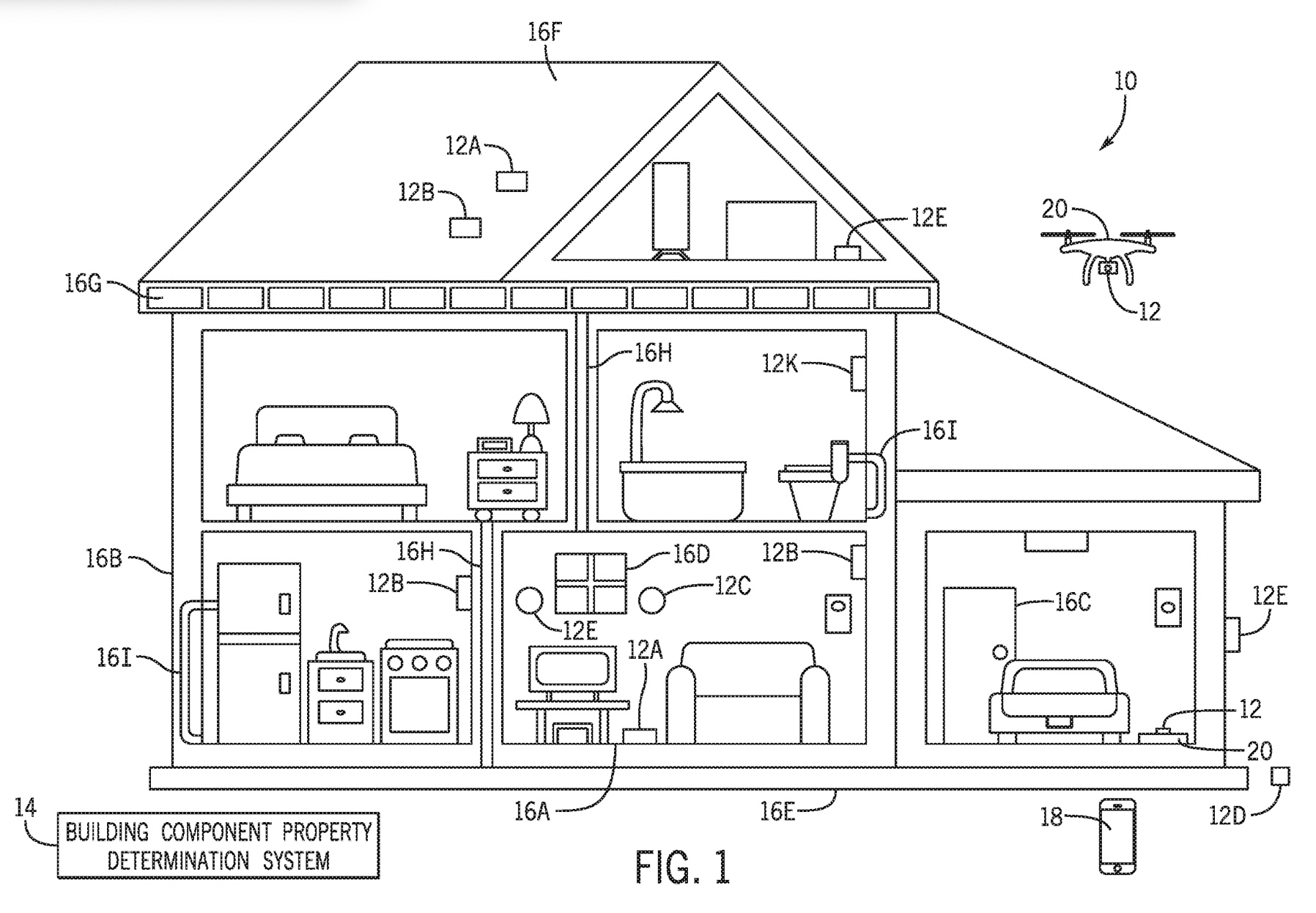
11,105,735. Detect the properties of building materials used in structures using non-destructive means via sensors. Great when appraising/insuring a home!
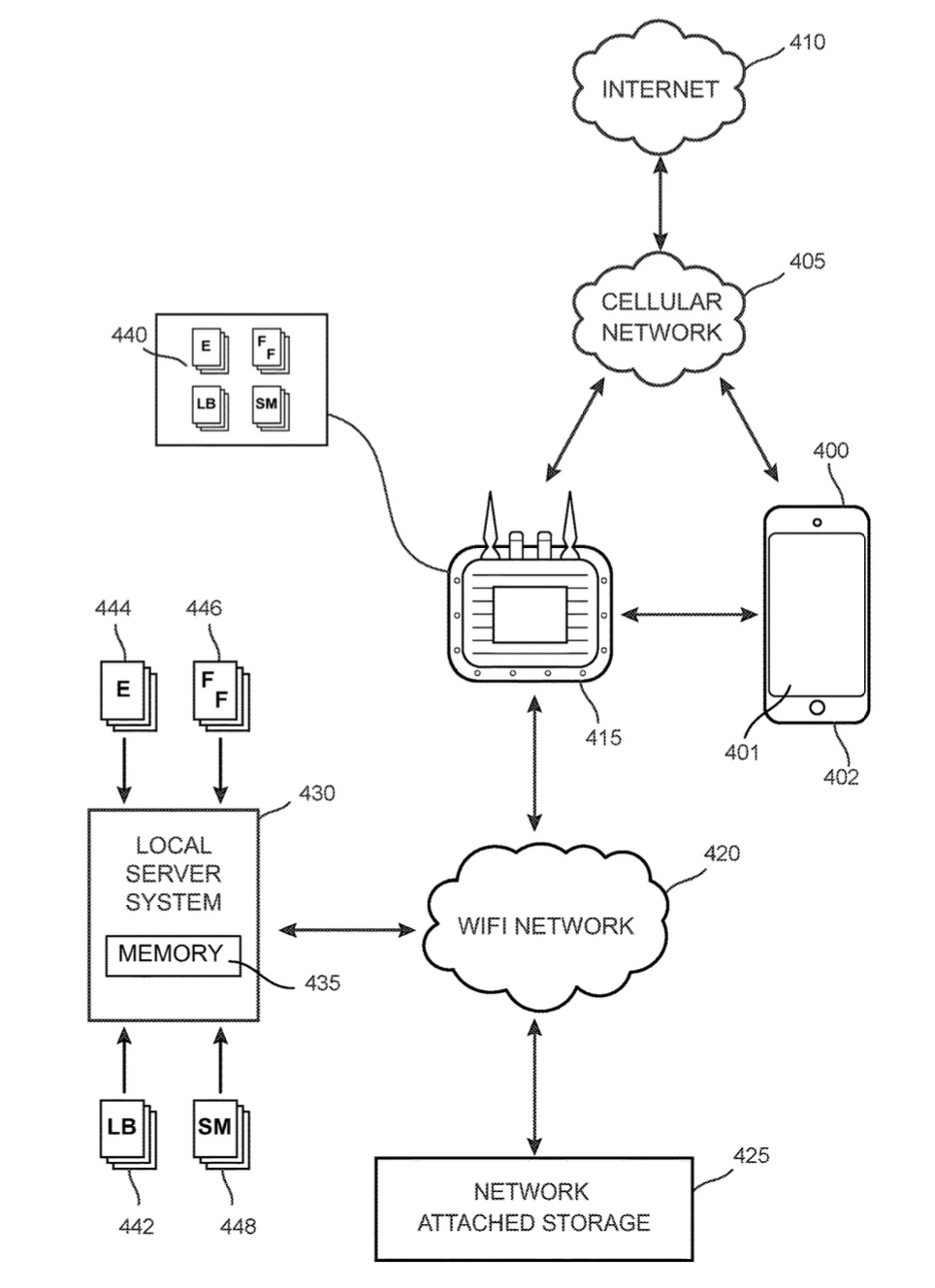
11,122,137. Think of putting proxies with caching and DNS caching on a router during large events, and that’s in the neighborhood of how this works. Reduce the network congestion at concerts and stadiums using this technology.
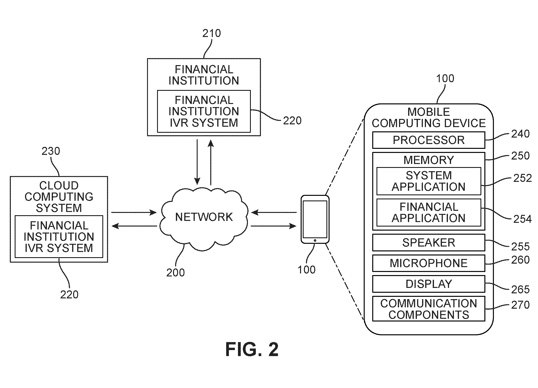
11,146,679. This enables IVR to send/receive files from the user’s device, and enables entire IVR trees to be pushed to the user’s handset to reduce load on central systems and frees up phone lines until one is requested from the endpoint IVR handling. It also allows a third system to take traffic to capitalize on 5G capability and more efficient network routes.
11,178,521. IVR meets phone tree, with security checks in place. Need to make exactly one phone communication which will trigger multiple or try from a list? This technology enables you to do so.
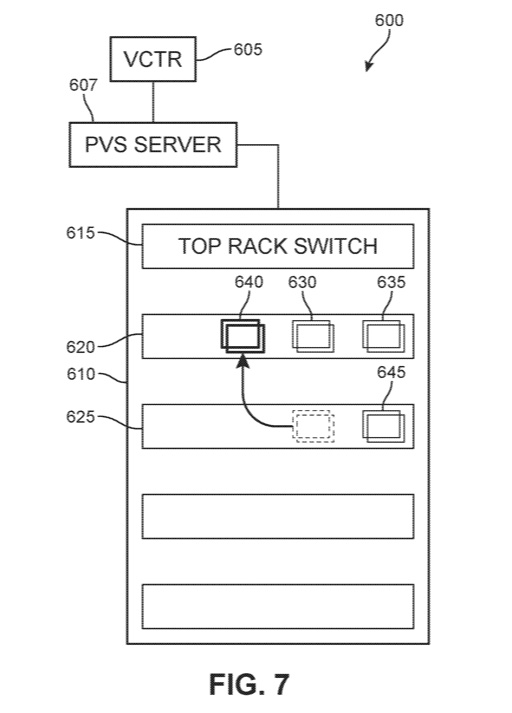
11,182,226. Enhance your application workload placement by ensuring that app communications aren’t going through unnecessary hops and instead preferencing that workloads reside closer to one another from a network perspective (e.g.: same host, same rack, even same subnet or tag can help), or as I like to call it, ‘netcworkicly’. This technology allows for both initial placement and recommendations after analysis. Works great for VDI too!
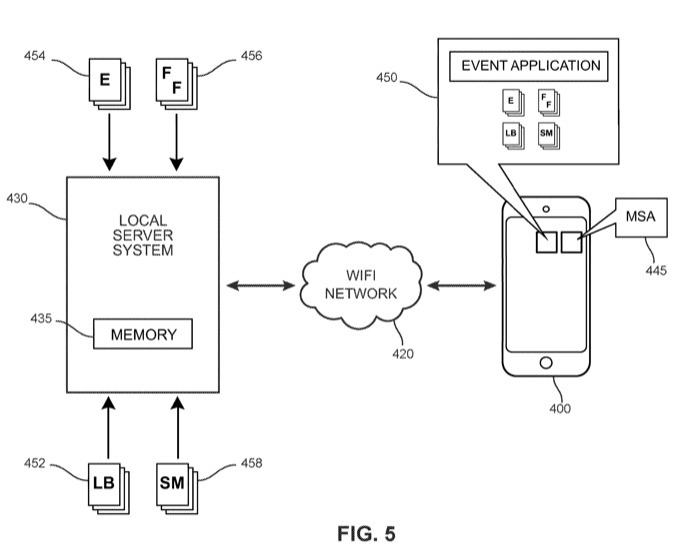
11,190,572. A novel method for determining and storing website data from high traffic websites in memory during a large event at an event location for access by mobile computing devices through an event application. I recommend using this in conjunction with a related one I invented: 11,122,137 for best results.
11,200,718. Enables homebuyers to see what their furniture would look like in a given house without needing to know any dimensions ahead of time. All of this is done in real time with extremely low latency.

Each titled Systems and methods for locally streaming applications in a computing system - 10,089,209 - 10,248,531 - 10,452,512 - 10,824,534 - 11,210,196. Want to eliminate the cruft that builds up over time in your computer? Want to eliminate breaking changes when you get new software/updates installed? That’s what this solves.
10,671,693 and 10,977,335- Systems and methods for online identity management. Stake your claim online, monitor your identity across multiple services, and automate your updates across every platform. Command your online presence in a single touch.
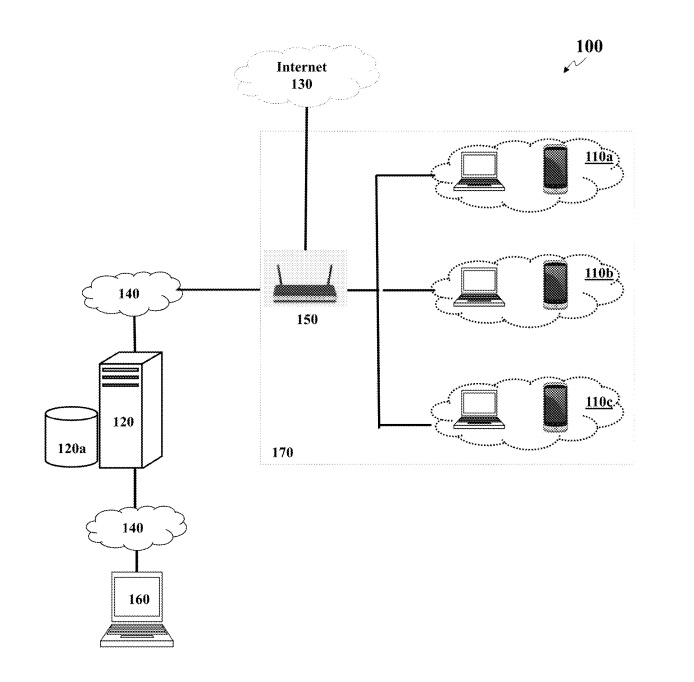
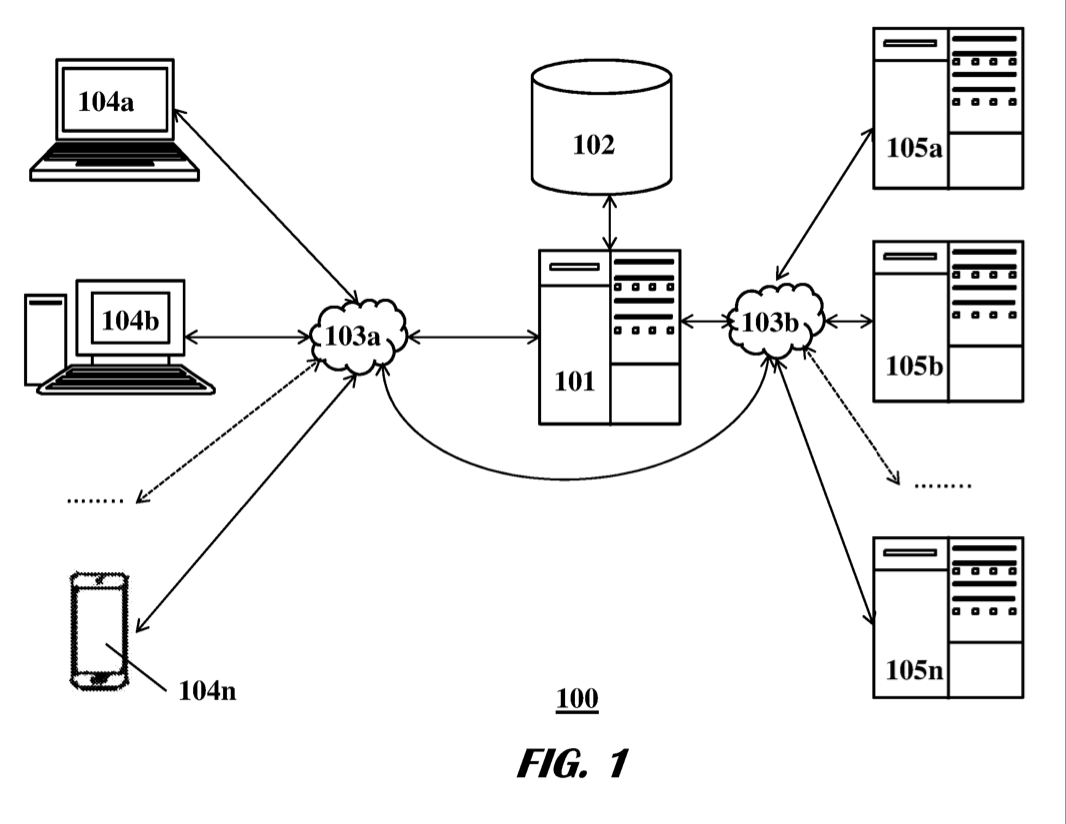
11,025,663 - Network Policy Automation. Automate your home and SMB network security with microsegmentation and coordinated privacy services to and between IoT devices. You shouldn’t need to be a security engineer to be safe in your own home!
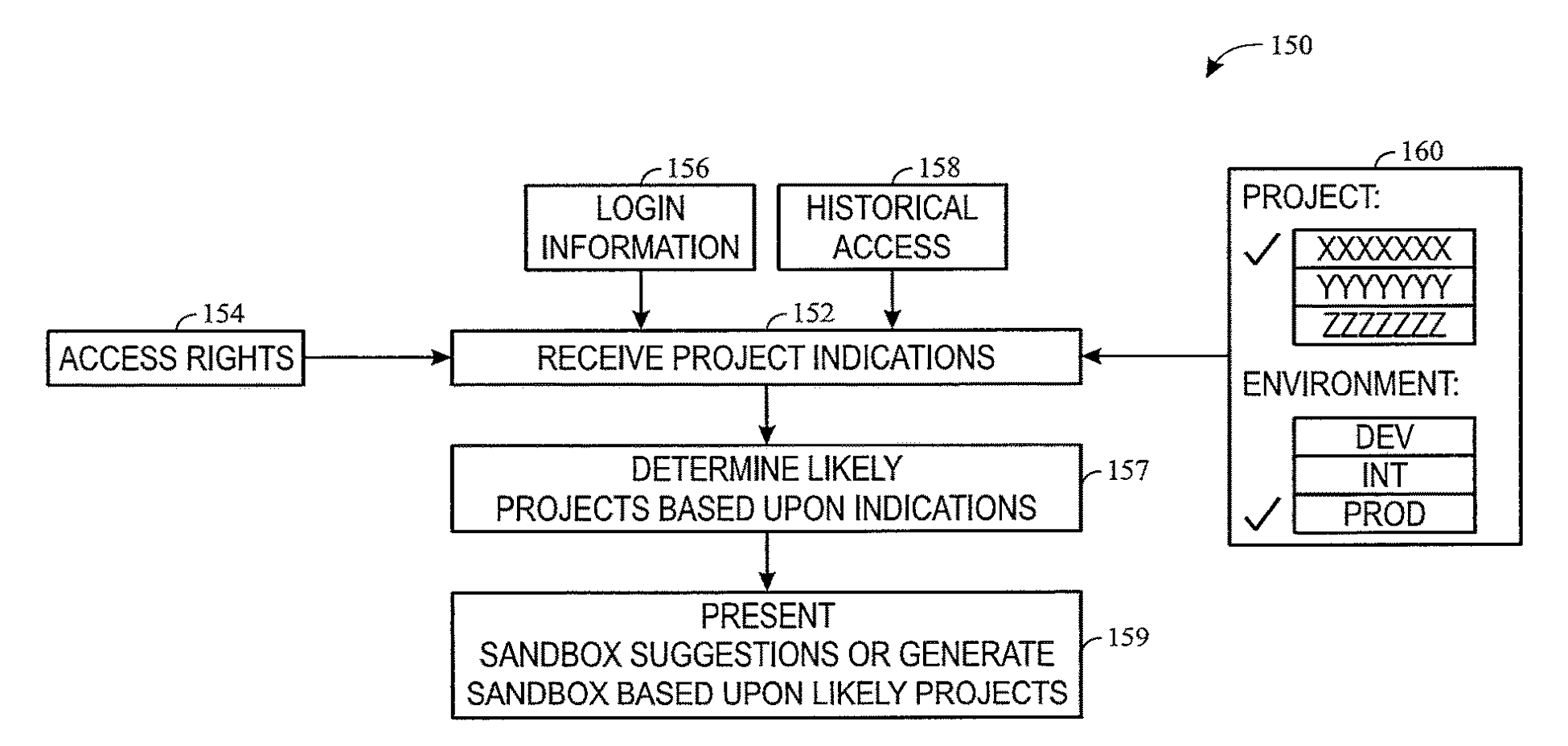
10,872,032 - Systems and methods for software development using sandbox views. Want to offer non-persistent user environments and be able to do development offloaded to the local machine? This enables that. Inspired by the challenges of non-persistent VDI, user profile virtualization, and needing a solution to enable development teams to use that architecture.
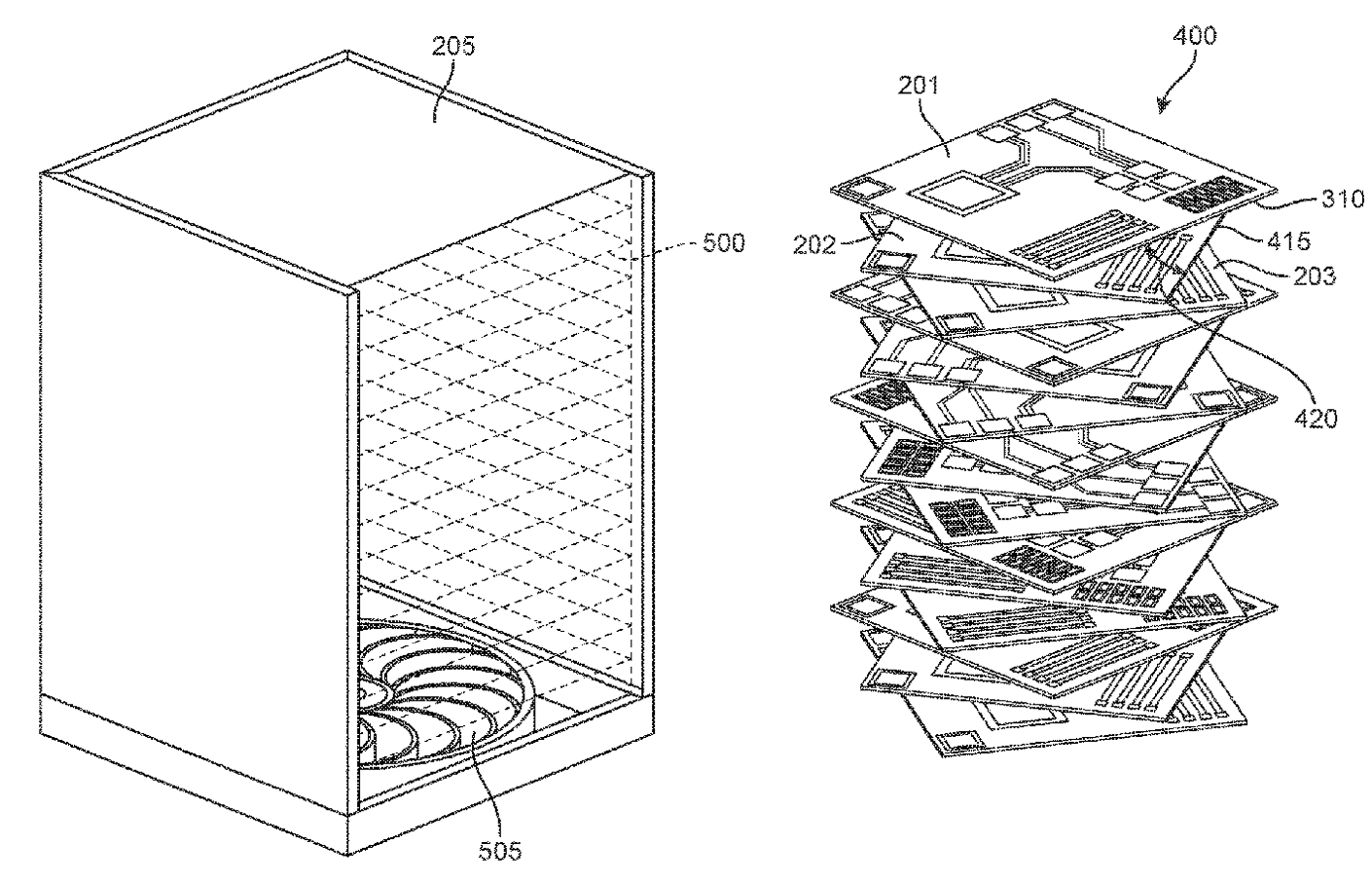
10,869,409. Take advantage of a vortex to accelerate heat removal in racks and lower your spend on air handling.
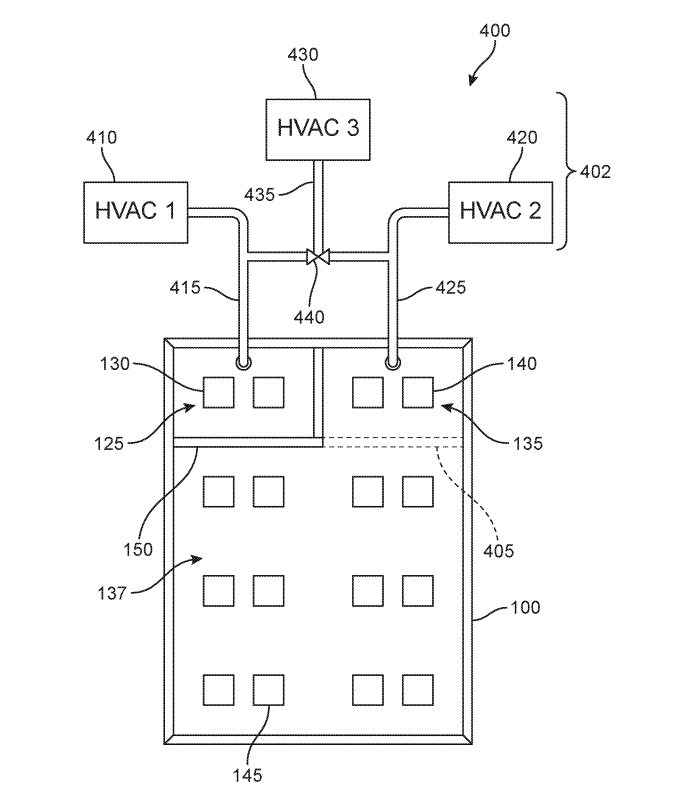
10,893,634. Your datacenter equipment doesn’t have the same requirements - why do we cool it as if it did? Use this to solve that, saving your cooling spend and keeping equipment in more stable environments.
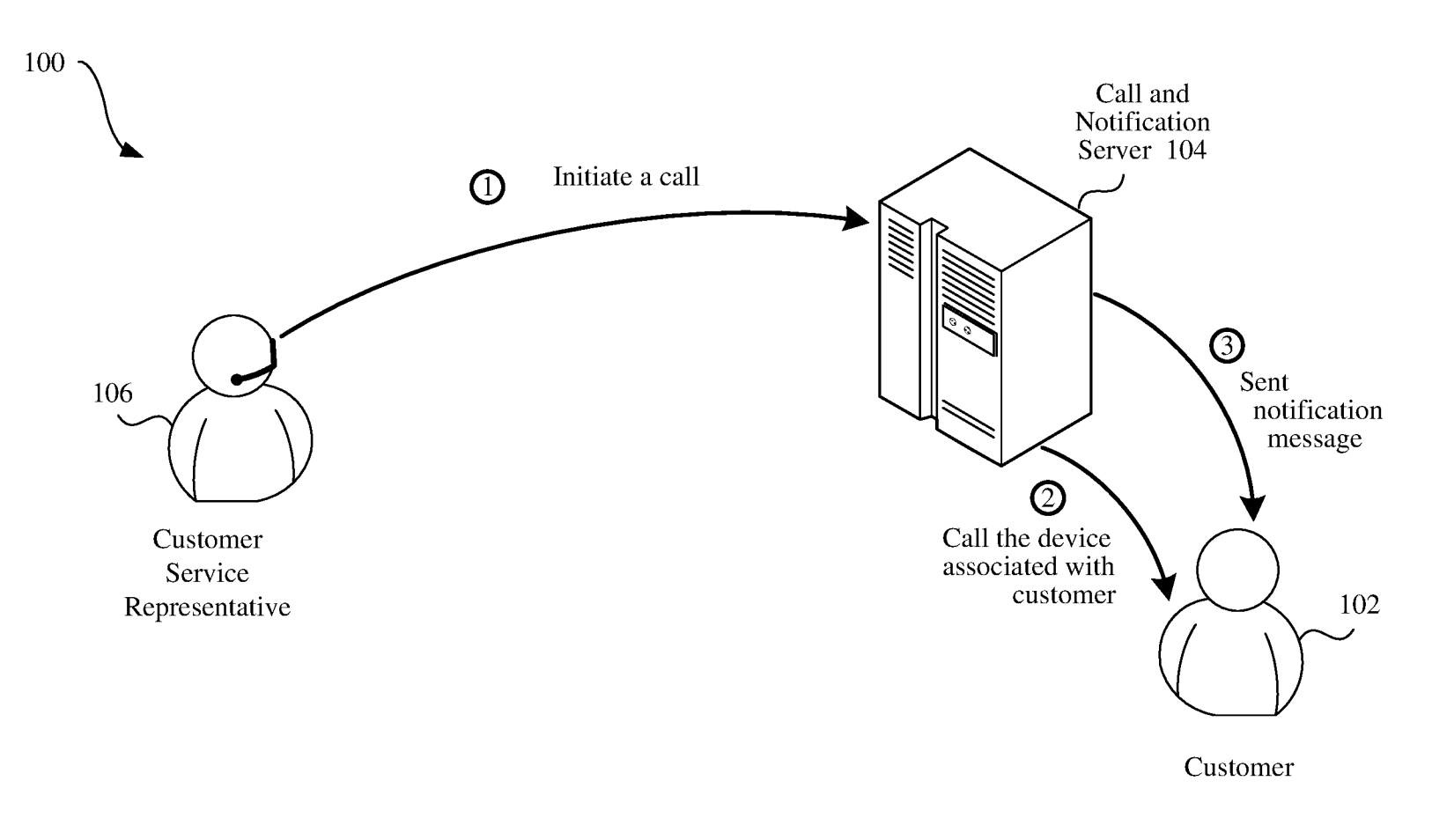
10,986,226. Prove that the customer service rep is truly with the company they say and fight fraud – this system would let a company send a push to users' devices when they need to reach the customer so that you know it’s really them.

11,105,735. Detect the properties of building materials used in structures using non-destructive means via sensors. Great when appraising/insuring a home!

11,122,137. Think of putting proxies with caching and DNS caching on a router during large events, and that’s in the neighborhood of how this works. Reduce the network congestion at concerts and stadiums using this technology.

11,146,679. This enables IVR to send/receive files from the user’s device, and enables entire IVR trees to be pushed to the user’s handset to reduce load on central systems and frees up phone lines until one is requested from the endpoint IVR handling. It also allows a third system to take traffic to capitalize on 5G capability and more efficient network routes.

11,178,521. IVR meets phone tree, with security checks in place. Need to make exactly one phone communication which will trigger multiple or try from a list? This technology enables you to do so.

11,182,226. Enhance your application workload placement by ensuring that app communications aren’t going through unnecessary hops and instead preferencing that workloads reside closer to one another from a network perspective (e.g.: same host, same rack, even same subnet or tag can help), or as I like to call it, ‘netcworkicly’. This technology allows for both initial placement and recommendations after analysis. Works great for VDI too!

11,190,572. A novel method for determining and storing website data from high traffic websites in memory during a large event at an event location for access by mobile computing devices through an event application. I recommend using this in conjunction with a related one I invented: 11,122,137 for best results.

11,200,718. Enables homebuyers to see what their furniture would look like in a given house without needing to know any dimensions ahead of time. All of this is done in real time with extremely low latency.

Each titled Systems and methods for locally streaming applications in a computing system - 10,089,209 - 10,248,531 - 10,452,512 - 10,824,534 - 11,210,196. Want to eliminate the cruft that builds up over time in your computer? Want to eliminate breaking changes when you get new software/updates installed? That’s what this solves.

10,671,693 and 10,977,335- Systems and methods for online identity management. Stake your claim online, monitor your identity across multiple services, and automate your updates across every platform. Command your online presence in a single touch.

11,025,663 - Network Policy Automation. Automate your home and SMB network security with microsegmentation and coordinated privacy services to and between IoT devices. You shouldn’t need to be a security engineer to be safe in your own home!

10,872,032 - Systems and methods for software development using sandbox views. Want to offer non-persistent user environments and be able to do development offloaded to the local machine? This enables that. Inspired by the challenges of non-persistent VDI, user profile virtualization, and needing a solution to enable development teams to use that architecture.

10,869,409. Take advantage of a vortex to accelerate heat removal in racks and lower your spend on air handling.

10,893,634. Your datacenter equipment doesn’t have the same requirements - why do we cool it as if it did? Use this to solve that, saving your cooling spend and keeping equipment in more stable environments.

10,986,226. Prove that the customer service rep is truly with the company they say and fight fraud – this system would let a company send a push to users' devices when they need to reach the customer so that you know it’s really them.